TARA Template
TARA TemplateISO/SAE 21434 is an international standard that establishes new regulations to replace existing vehicle life cycle standards as both electronic control of vehicles and external access routes to vehicles increase. As a part of this, TARA (Threat Analysis and Risk Assessment) is a methodology that quantitatively analyzes vehicle cybersecurity threats and helps users set appropriate response measures.
The "Cybersecurity TARA Template for Automotive Polarion" project template developed by Branvi Inc. based on ISO/SAE 21434 and TARA methodology allows users to identify assets, classify threats to assets, and select appropriate actions according to risk level.

You can check the progress of the TARA methodology at a glance and quickly access to each step.
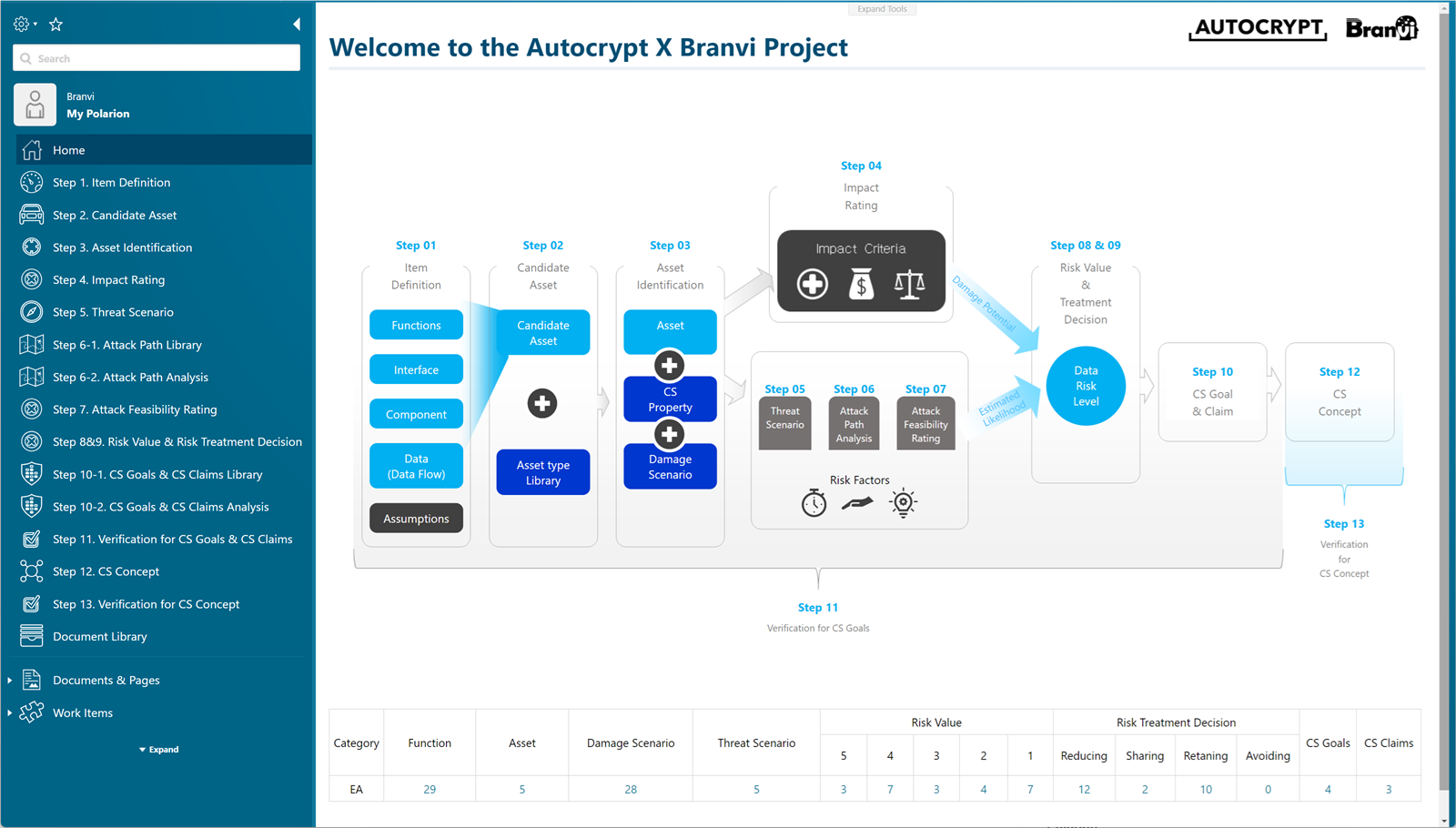
Define the items for which you want to analyze security threats and the logical, physical, and electronic configurations connected to them.

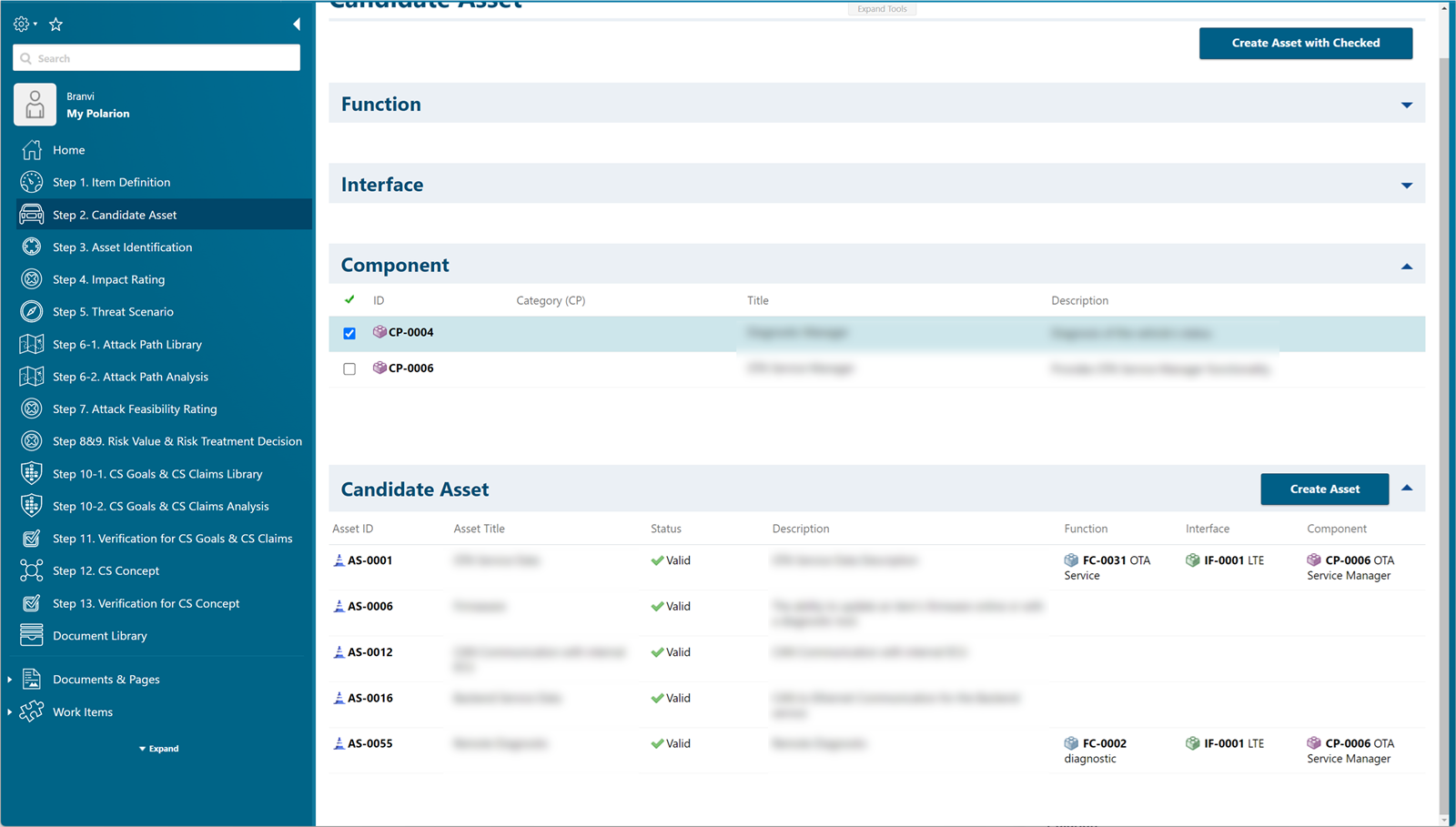
Identify assets based on the configurations created in the previous step and determine whether the identified assets can become threats.
Check the asset information and compare it with the appropriate type in the global project, directly identify Cybersecurity Properties that may be damaged, or create a damage scenario to analyze the asset.
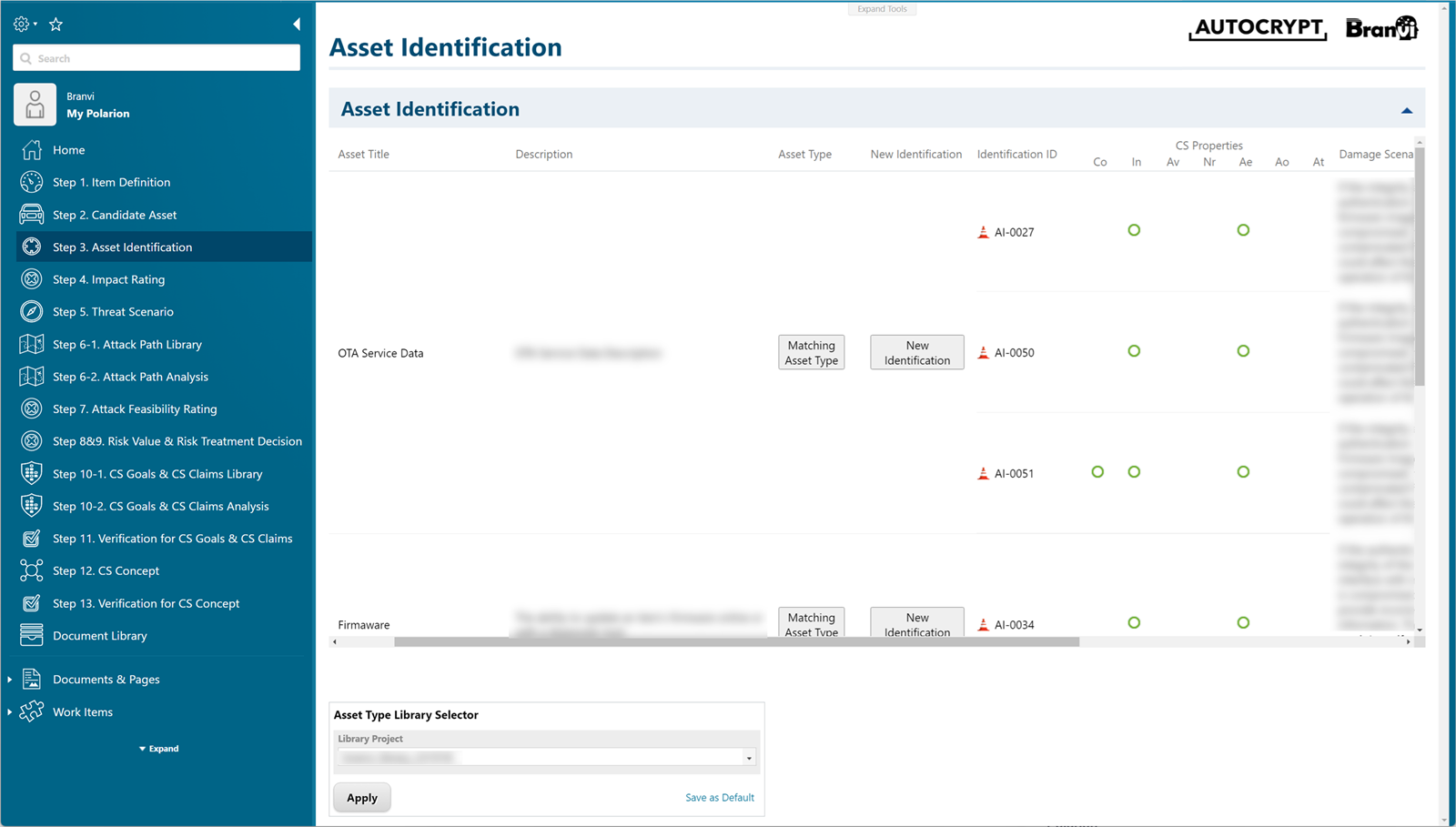
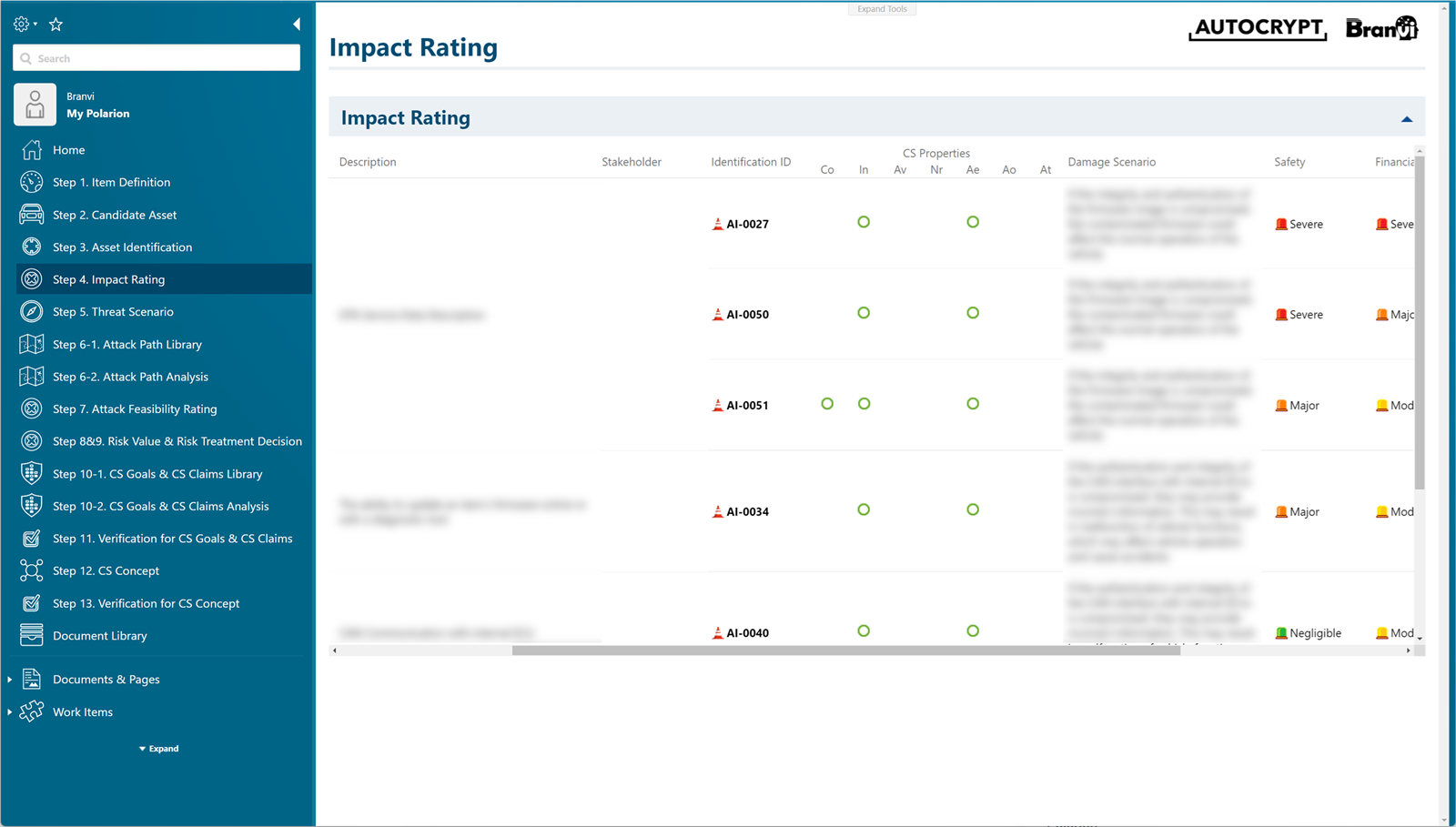
Determine the impact by each sector through the identified Cybersecurity Properties and Damage Scenarios and measure the final aggregated Impact Rating.
Based on the compromised Cybersecurity Properties, predict which attack methods can threaten the asset and create a threat scenario.

Create an attack path and feasibility to the asset, and analyze the attack path that can respond to the threat method.
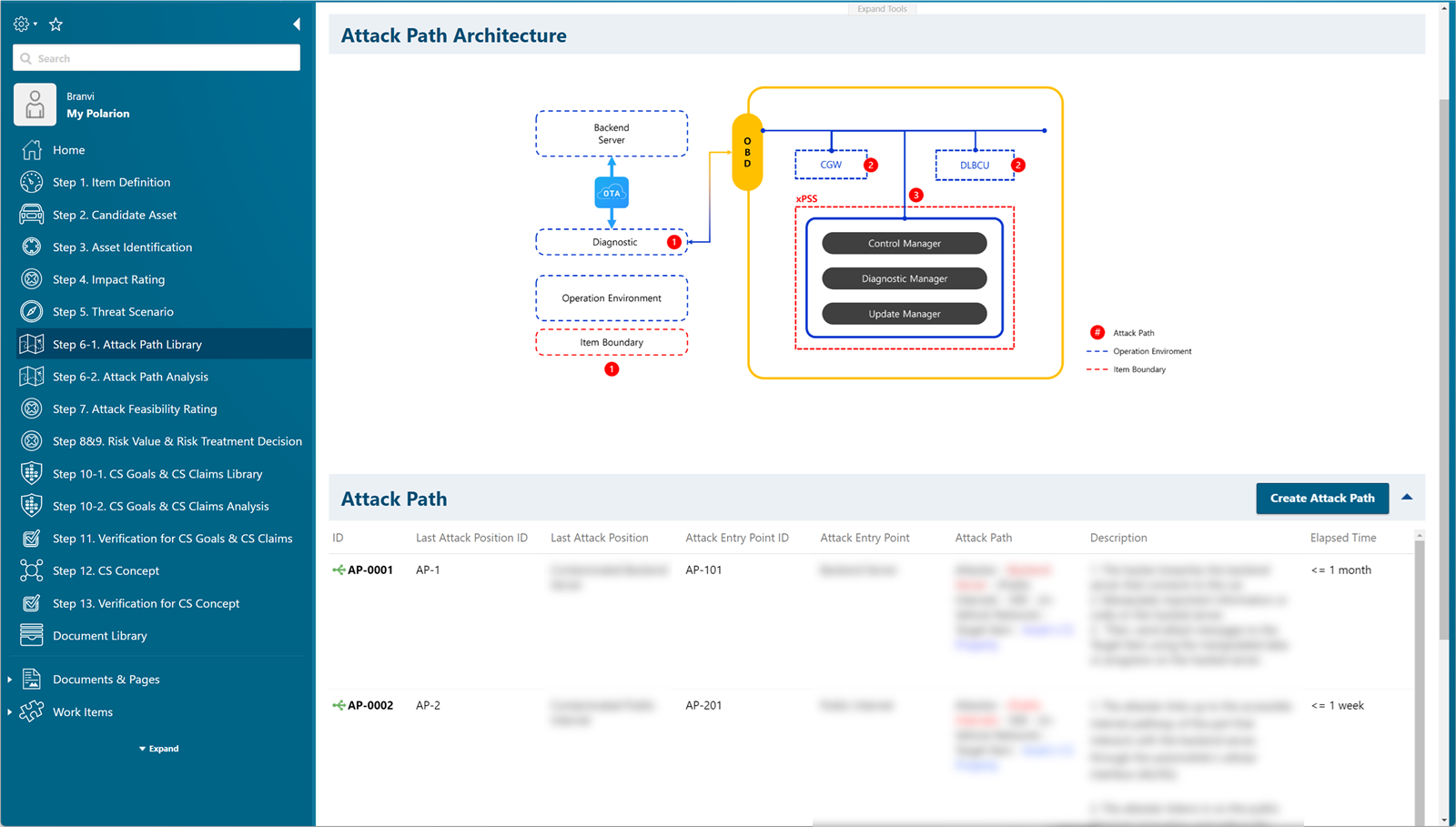
Calibrate predefined feasibility information through threat analysis and attack path information.

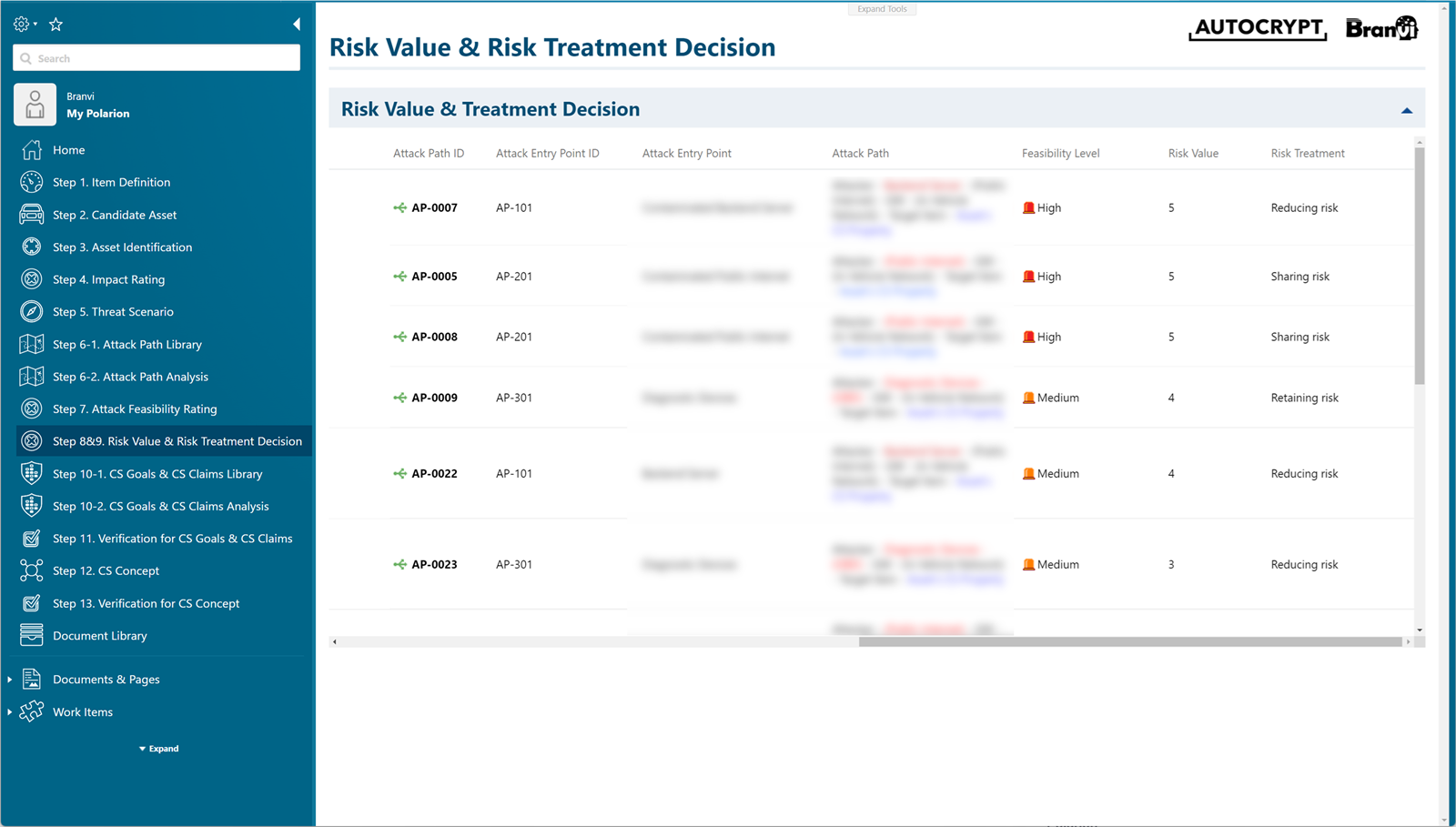
Using the predefined standard Risk Matrix based on the previously assessed impacts and feasibilities, the TARA Template guides users to automatically classify the risk levels and choose how to respond.
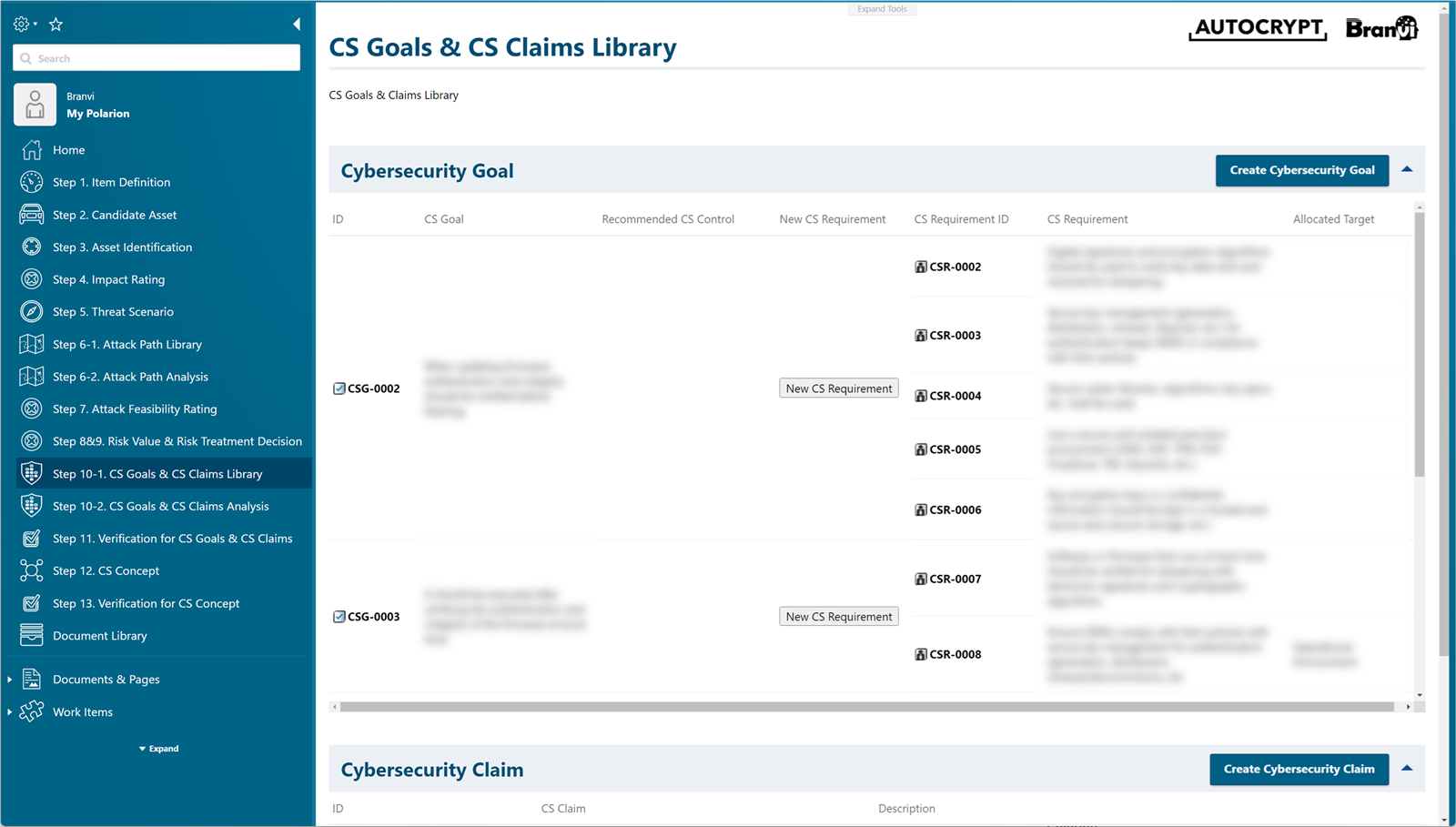
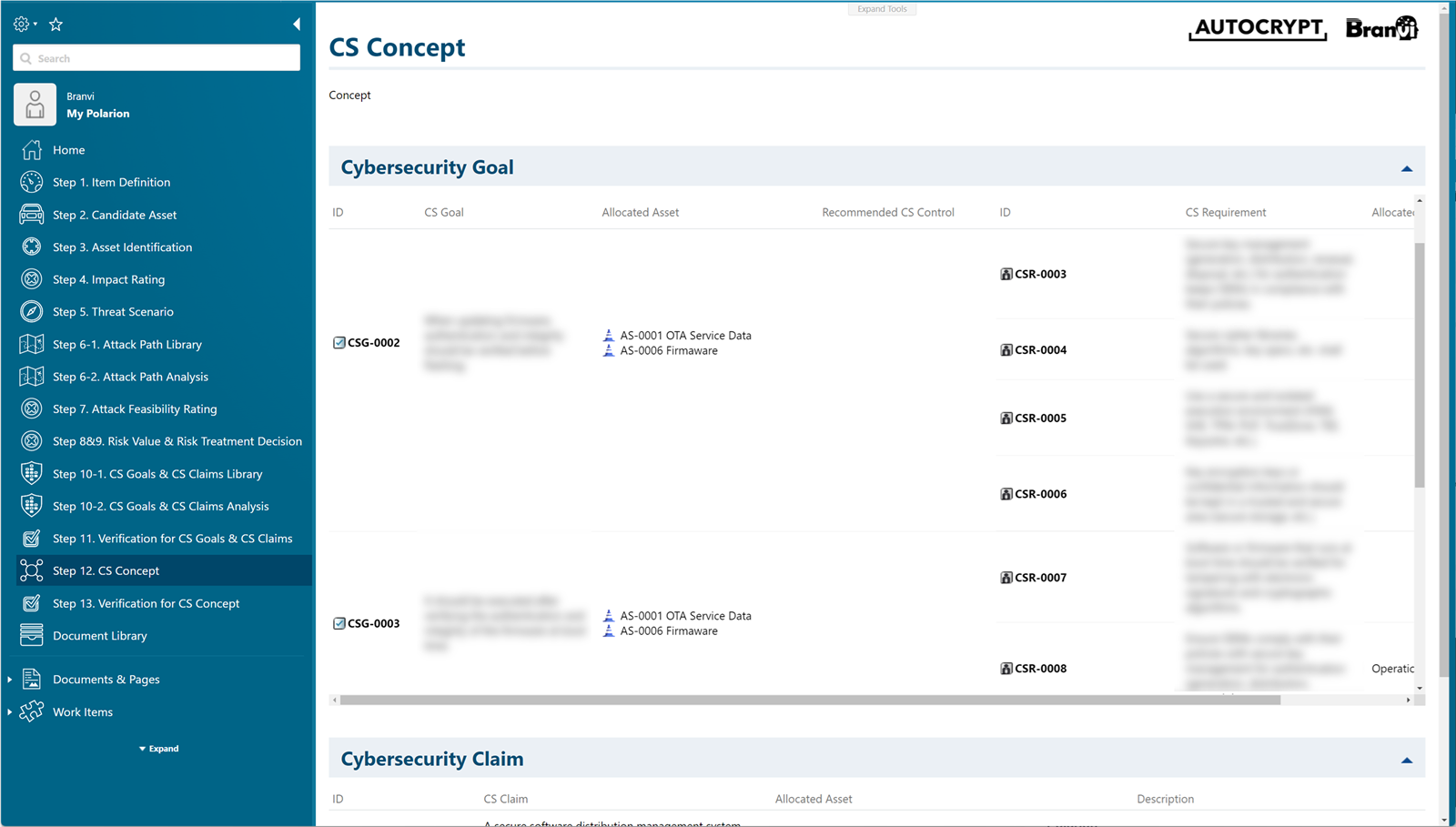
Create Cybersecurity Goals, Cybersecurity Requirements connected to them, and a Cybersecurity Claims in advance, and connect the Cybersecurity Goals or Cybersecurity Claims according to Risk Treatments.
Review whether a series of processes has been successfully completed using verification criteria prepared for the cybersecurity information obtained while the users proceed with the project.
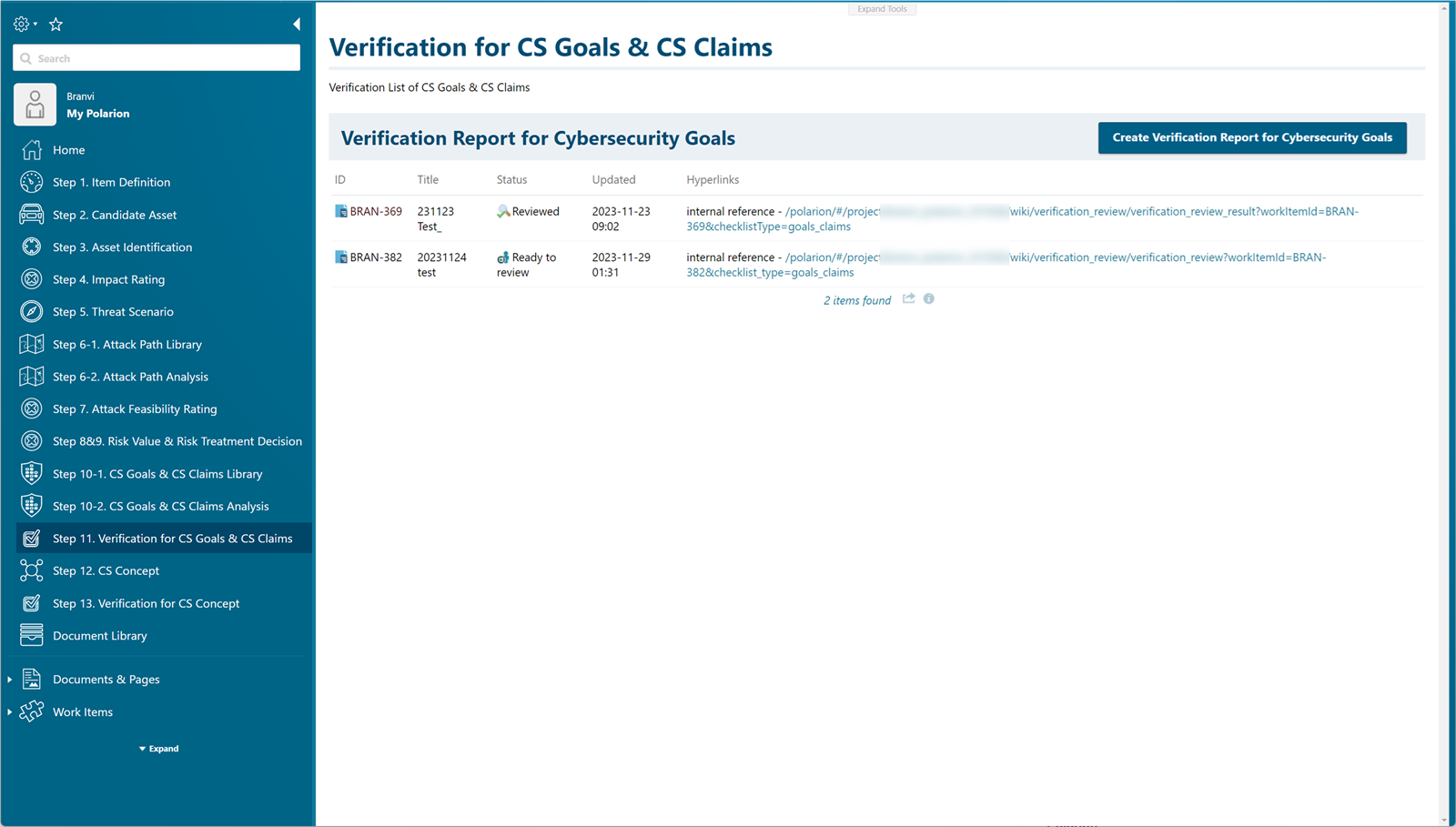
Check which assets are related to the defined Cybersecurity Goals and Cybersecurity Claims.
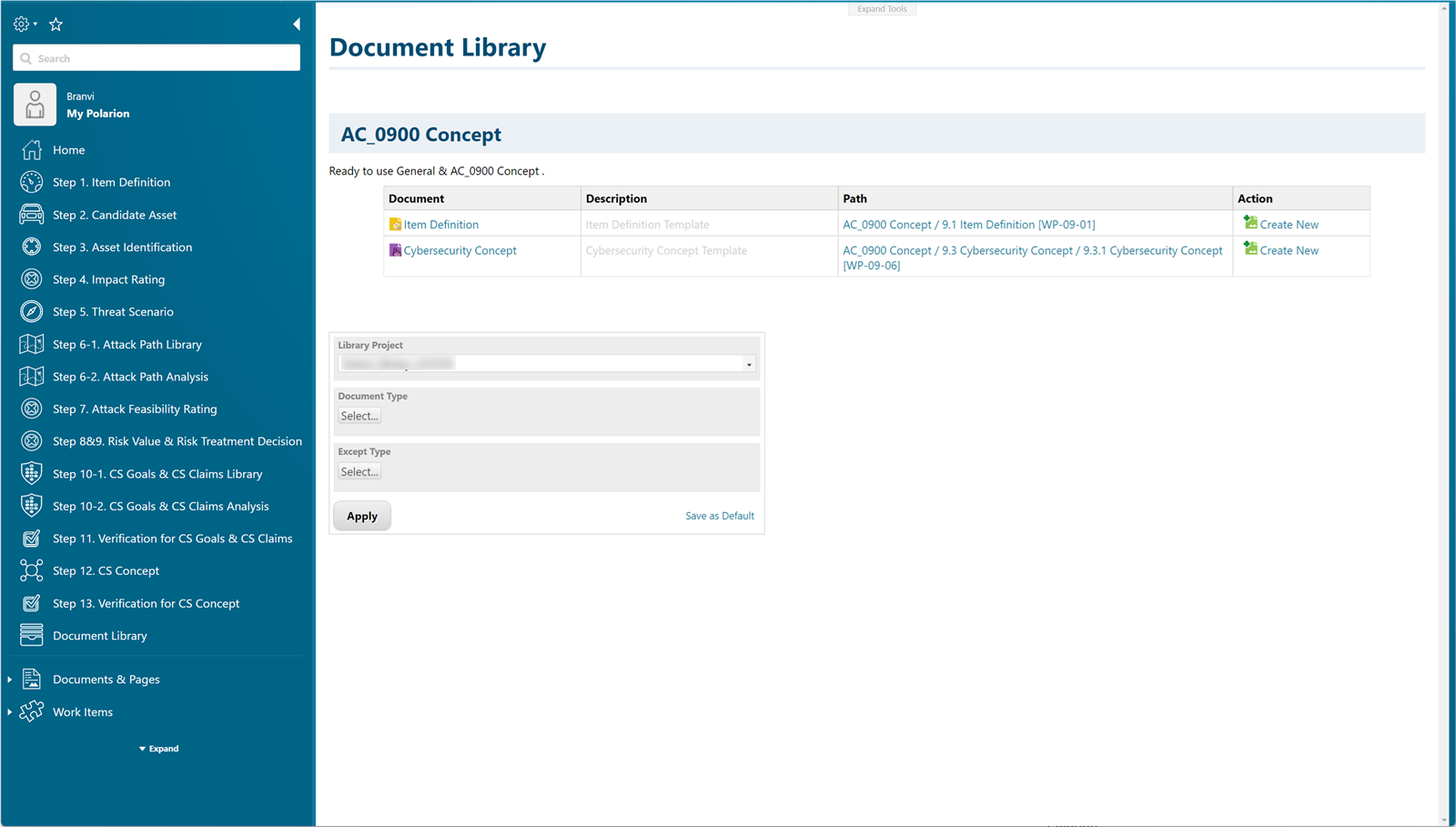
Provide libraries of related documents to help you write quickly and provide easy version control.